Passwords have become increasingly prevalent and complex. Indeed, the average user has around 90 accounts to manage. With so many accounts, users tend to rely on short, simple, and ineffective passwords, often reusing them on many accounts.
Incomplete Solutions
To address this issue, people have developed several solutions:
- OAuth2 – Users can authenticate by signing in with their Google, Facebook, Twitter, or Github account. Through these means, users only need to remember one password: that of the password provider. Although convenient, it can be cumbersome to remember which account one used to sign in and whether one used Google, Facebook, or some other provider. In addition, there are important ramifications for privacy–the provider can link which websites or services that a user uses and also forces browsers to accept some cross-site cookies in order for this authentication flow to work. Furthermore, this gives more power to platforms whereby a ban from a Google or Facebook account could likely lock people out of all accounts that are secured through it.
- Password-less logins – Users sign in by clicking a link in their email. While these systems seem promising and don’t require too many changes, they are also limited in its prevalence.
- Security keys – Although they are designed to be replacements to passwords in the future, they still don’t have enough prevalence on the web yet. Furthermore, it requires major overhauls to the authentication system, limiting its availability and thus its impact for the near future.
- Password managers – Despite password managers’ increased prevalence and utility, most users overwhelmingly still rely on memorization, fearing that password managers are unsafe or contain backdoors from government agencies, or due to habits.
While these solutions seem promising, they are still second-class citizens on the web. Simply put, passwords are a deep-seated de facto standard of the web, and they are not going away anytime soon.
Password Reuse
In recent times, password breaches have increased, revealing millions of passwords. As of this year, Have I Been Pawned reported over 340 breaches since its inception. This isn’t surprising considering that many people are reusing their passwords, making password spray attacks extremely effective.
While it might be difficult to discourage password reuse or even to improve upon current solutions to passwords, one thing is sure: we can make better passwords if we can find a way to put the right amount of entropy, or randomness, into our passwords. However, humans tend to pick non-random words, often opting for the simple “password123” or its counterparts. If we take humans out of the equation, however, we can guarantee the time it takes for a person to crack a password, ensuring, mathematically speaking, that the password is secure. But these randomly generated passwords are difficult to memorize.
Polydice
An exceptional alternative is diceware, a provably secure system for generating passwords. By rolling dice several times, we can generate a password by searching a reference table for the word that corresponds to your dice roll.
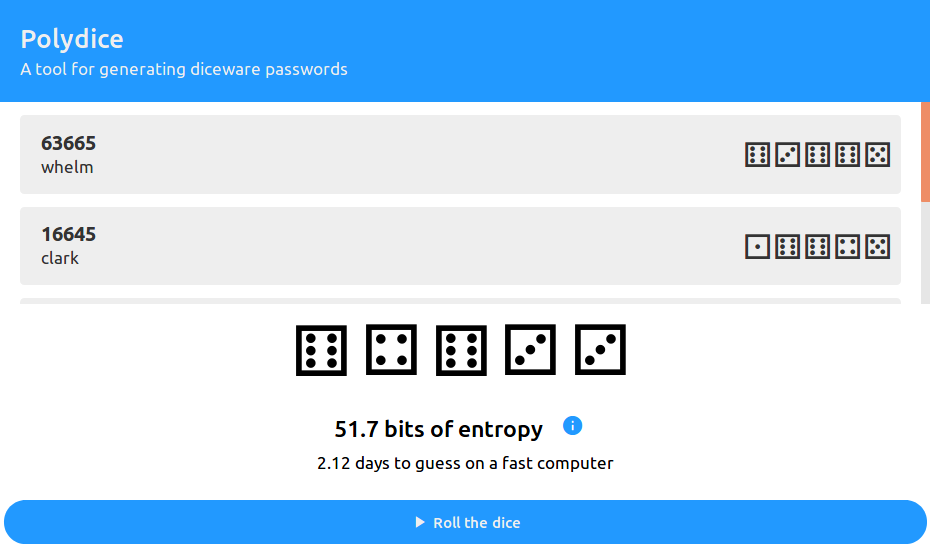
In that list, there are 7,776 words. These words can be concatenated together to form your password. To generate a secure password, you would need at least 6 words, resulting in 30 dice rolls. This can be tedious, so I created Polydice, software to help you generate a password.
Using Polydice
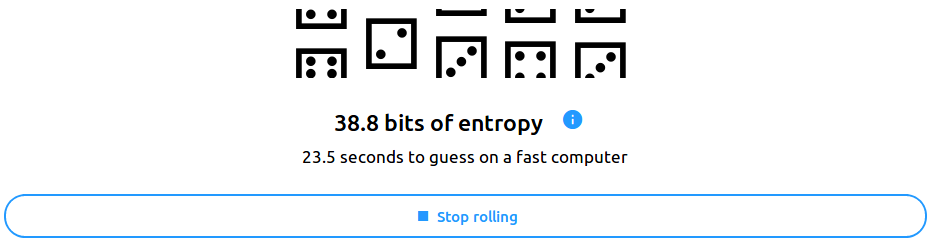
- Click start rolling on the bottom of the screen.
- Click stop rolling when you feel like it.
- Repeat steps 1 and 2 until the you have a sufficient password strength that you are comfortable with
- To generate a new password, reload the page.
Related posts
Must-reads
Towards Efficient Multiplication

Why life needs entrepreneurial thinking: How making goals is like starting a business
A Javascript Developer's Guide to Contributing to Firefox

Midway Through the Years